High-Level AWS Deployment
This guide provides a high-level AWS deployment overview. In this tutorial, you will learn examples of AWS deployment topology.
Prerequisites
Ensure that you have done the following:
- A namespace
- An account that will be used for the Infrastructure and KMS Stacks installations.
Base Infrastructure
- KMS Stack
- Core Stack
Expansion Node Infrastructure
- KMS Stack
- Node stack
Roles
- Infrastructure Administrator: Deploys the core and expansion node stacks. He/she also maintains the resources in each stack.
- Node Administrator: Deploys the KMS Stack for a node and manages the configuration and API key for the node.
Note:
One person can have multiple roles or a dedicated role. The greater separation of roles, the higher security of your system.
We highly recommend for you to NOT assign one person to be multiple Node Administrators as this does not represent a true MPC Configuration.
Deployment Topology Examples
Recommended AWS Configuration for Blockdaemon Builder Vault
This section outlines the optimal configuration setup for the Blockdaemon Builder Vault on AWS. The configuration ensures the highest security standards for multi-party operations.
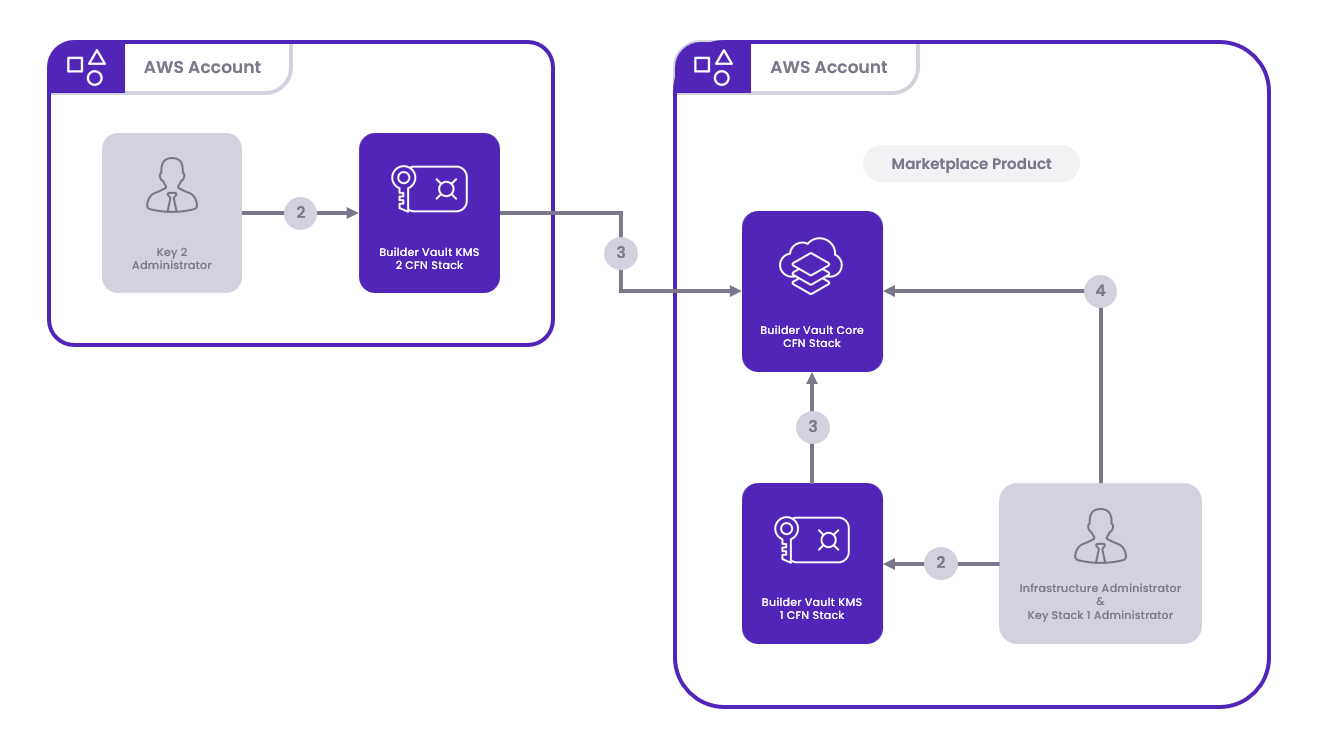
Components
The following components are essential for the setup:
- Builder Vault Core
- KMS Stack 1
- KMS Stack 2
Deployment Topology
Each KMS Stack should be deployed in separate AWS accounts for enhanced security through multi-party operations. This separation maximizes the security threshold. However, deploying one of the KMS Stacks within the same AWS account as the Builder Vault Core is recommended to facilitate effective debugging by infrastructure administrators. This setup allows for streamlined troubleshooting of a single node during configuration changes.
Deployment Process
- Account Selection: Decide which AWS account will be used to deploy the Builder Vault Core. Share the selected account's ID among all parties. The KMS Stack input parameter will utilize this Account ID to indicate the deployment's location.
- KMS Stack Deployment: Key administrators will deploy the KMS Stack within their chosen AWS Account and Region. This choice is independent of the Core's deployment location.
- SSM Parameter Sharing: The infrastructure administrator will request the SSM parameter outputs from the key administrators necessary for connecting the components.
- Core Stack Deployment: After receiving the SSM outputs, the Infrastructure Administrator will deploy the Core stack in the AWS account selected in the initial agreement.
Recommended Node Expansion for Blockdaemon Builder Vault
This section outlines the recommended node expansion setup for the Blockdaemon Builder Vault on AWS.
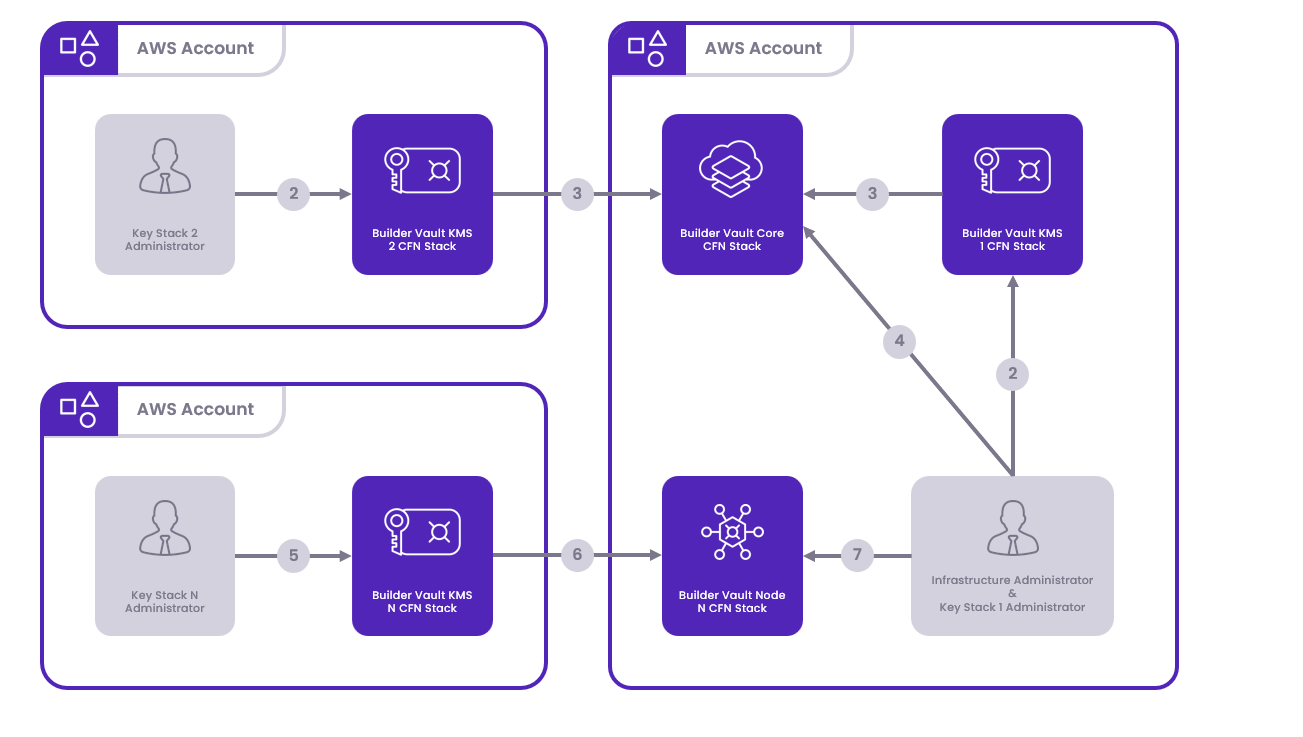
Components
The following components are essential for the setup:
- Builder Vault Core
- Builder Vault Node
- Builder Vault Key (2+N)
Deployment Topology
The node expansion uses a topology that allows adding nodes to the Builder Vault Core via the Builder Vault Node. This setup is designed to preserve the integrity of multi-party security by deploying each component into distinct AWS accounts. The KMS Stacks are region-flexible to meet data residency needs.
Deployment Process
- Account Selection: Decide which AWS account will be used to deploy the Builder Vault Core. Share the selected account's ID among all parties. The KMS Stack input parameter will utilize this Account ID to indicate the deployment's location.
- KMS Stack Deployment: Key administrators will deploy the KMS Stack within their chosen AWS Account and Region. This choice is independent of the Core's deployment location.
- SSM Parameter Sharing: The infrastructure administrator will request the SSM parameter outputs from the key administrators necessary for connecting the components.
- Core Stack Deployment: After receiving the SSM outputs, the Infrastructure Administrator will deploy the Core stack in the AWS account selected in the initial agreement.
- Expand with KMS Stack N: The respective KMS Stack N Administrator deploys their KMS Stack in a chosen AWS account and region for each additional node.
- Gather Additional SSM Outputs: The Infrastructure Administrator requests SSM parameter outputs from the KMS Stack N Administrators for new nodes.
- Deploy Node Stacks: The Infrastructure Administrator deploys each Builder Vault Node stack, incorporating the keys obtained from the Key Administrators.
- Synchronize Nodes: Restart EC2 instances of existing nodes to ensure recognition of the newly added node.
High-Security Configuration for Blockdaemon Builder Vault
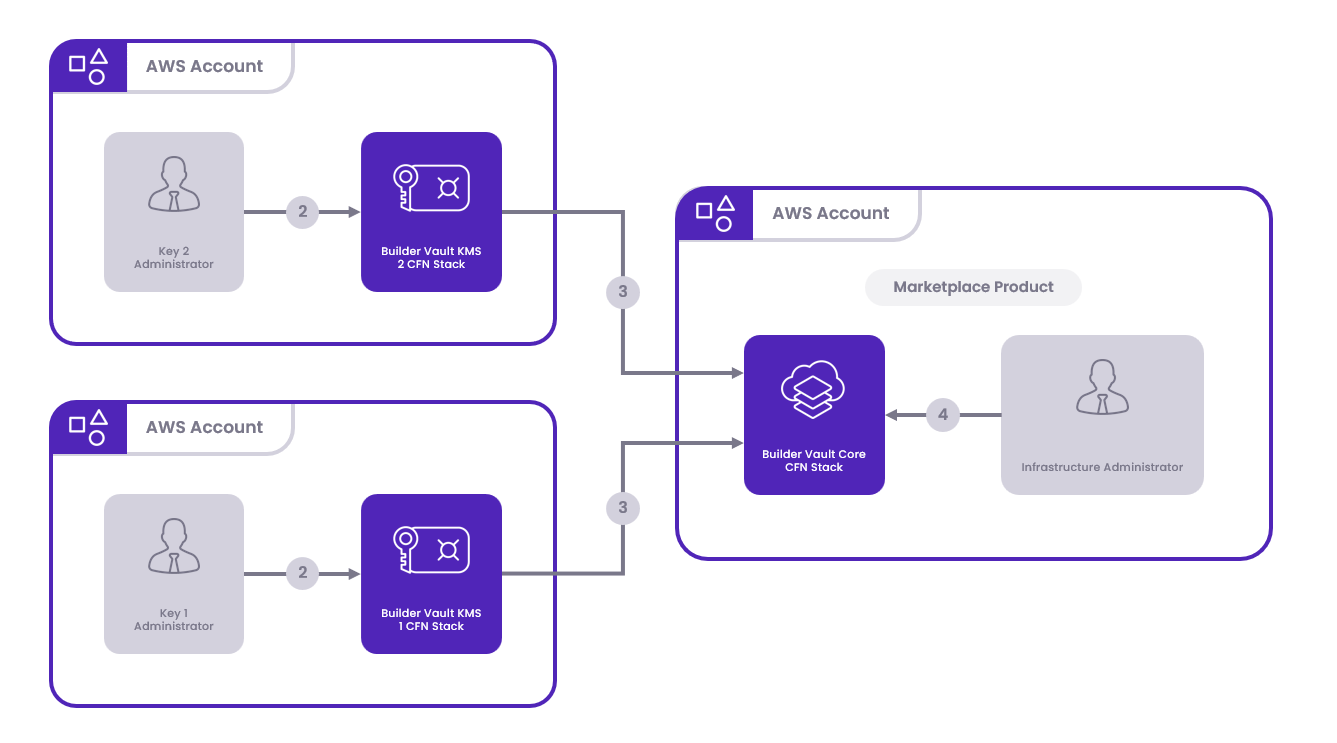
Components
The following components are essential for the setup:
- Builder Vault Core
- Builder Vault Key 1
- Builder Vault Key 2
Deployment Topology
If you don't want your infrastructure administrator to be a node administrator, you can deploy the core stack with three individuals who have a separate node administrator for Node 1. This topology has the highest level of security as it requires collusion between more parties to compromise the system.
However, this topology comes with the tradeoff that the infrastructure administrator cannot debug any of the nodes without direct involvement from a node administrator.
Deployment Process
- Account Selection: Decide which AWS account will be used to deploy the Builder Vault Core. Share the selected account's ID among all parties. The KMS Stack input parameter will utilize this Account ID to indicate the deployment's location.
- KMS Stack Deployment: Key administrators will deploy the KMS Stack within their chosen AWS Account and Region. This choice is independent of the Core's deployment location.
- SSM Parameter Sharing: The infrastructure administrator will request the SSM parameter outputs from the key administrators necessary for connecting the components.
- Core Stack Deployment: After receiving the SSM outputs, the Infrastructure Administrator will deploy the Core stack in the AWS account selected in the initial agreement.
Demo Configuration for Blockdaemon Builder Vault
This section details the recommended configuration for a demo deployment of the Blockdaemon Builder Vault within AWS.
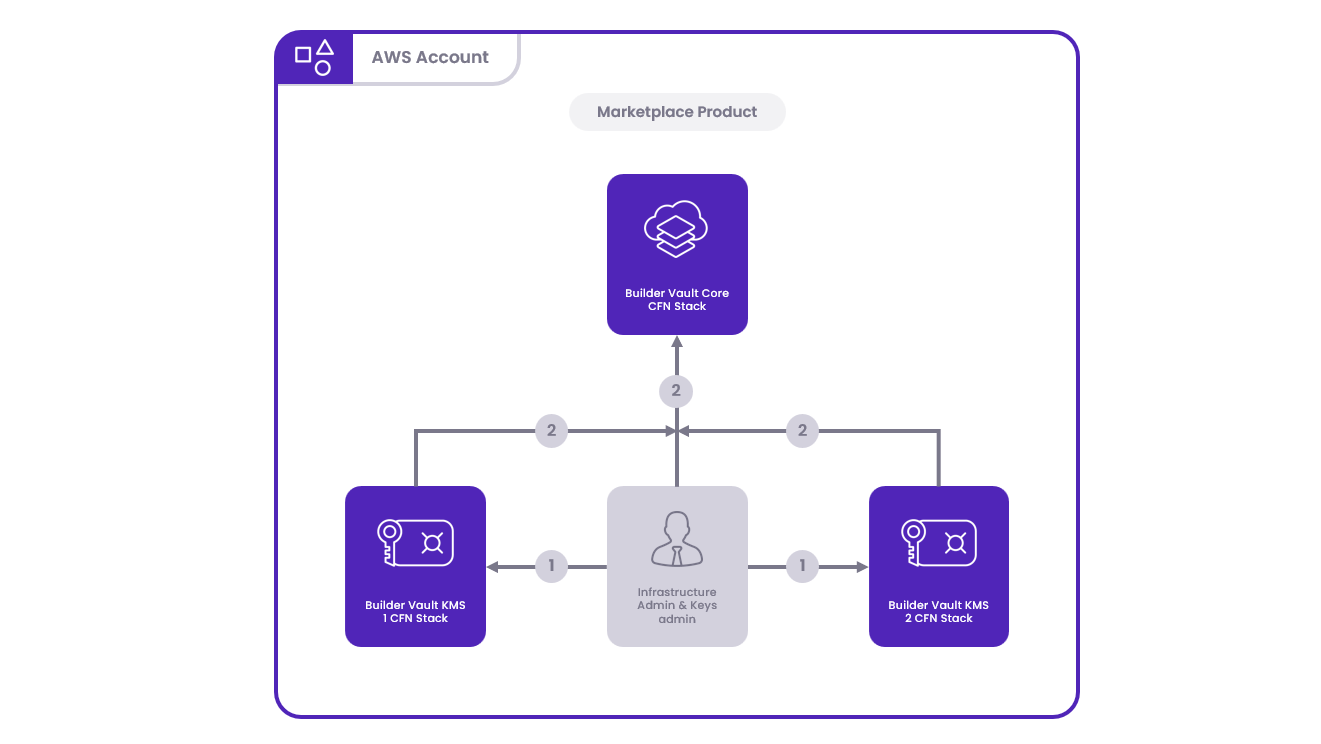
Components
The following components are essential for the setup:
- Builder Vault Core
- Builder Vault Key 1
- Builder Vault Key 2
Deployment Topology
Blockdaemon Builder Vaults can even be deployed by only one admin, for testing or demonstration purposes. However, this is not a recommended topology for any production use-cases, as it does not have any separation of node administration, which is the basis for MPC.
Deployment Process
- KMS Stacks Deployment: Initiate the deployment of KMS stacks within the designated AWS account, ensuring you capture the SSM parameter output from each KMS Stack.
- Core Stack Integration: Provide the collected SSM parameter outputs to the Builder Vault Core deployment process to complete the configuration.
Updated about 1 month ago